We are often asked about areas where customers overspend on Amazon Web Services (AWS). NAT gateway costs are high due to misplaced data transfers and are definitely near the top of our list.
This article will walk you through five steps you can take to find out which data transfers you’re overspending on and how you can eliminate those excess charges.
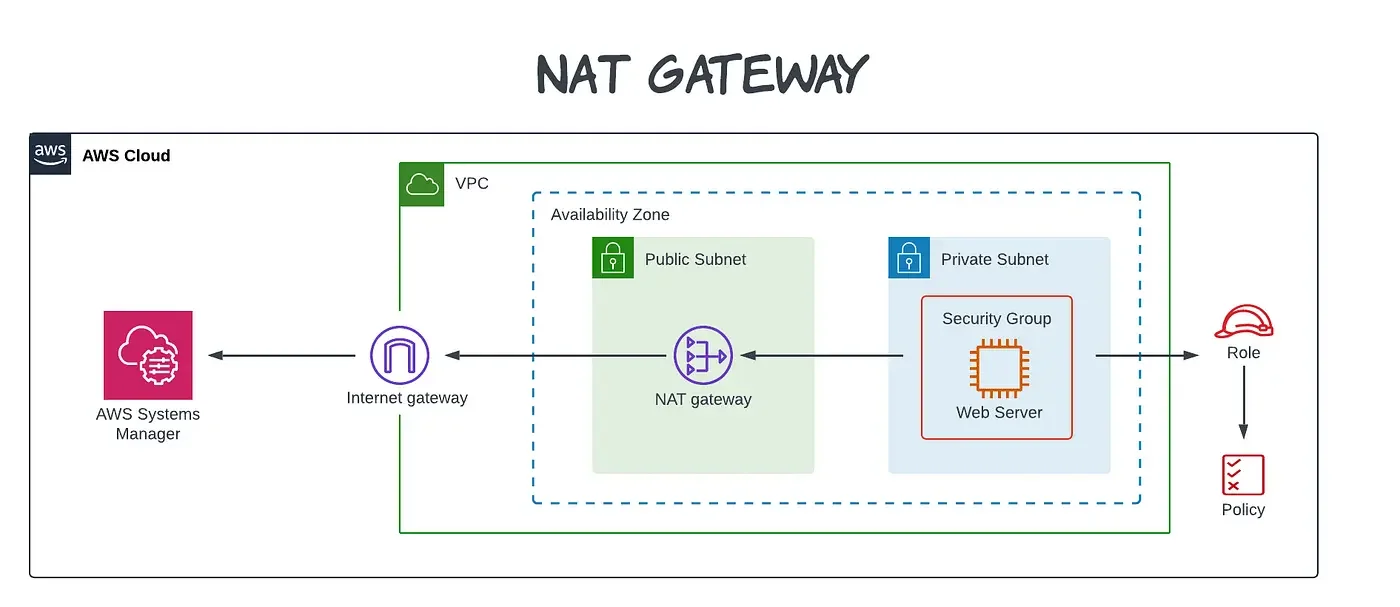
What Is A Nat Gateway?
Credit: AWS
A Network Address Translation (NAT) gateway is an AWS-managed, highly-available service that enables you to connect instances within a private subnet of an Amazon Virtual Private Cloud (VPC) to the internet.
This is because private subnets do not have a way to connect to the Internet (a path to an internet gateway).
How Do NAT Gateways Work?
NAT gateways allow your private network to communicate with the internet or other public networks. You can use them to send and receive traffic from a single IP address without revealing your hosts’ identities. NAT gateways help secure instances within your private network by blocking all ingress traffic and allowing egress traffic.
A great use case for this is when you’re ready to push out software updates across your organization but don’t want to give software update servers from the internet direct access to devices on your private network.
Here’s a quick look at how a NAT gateway works inside the AWS public cloud.
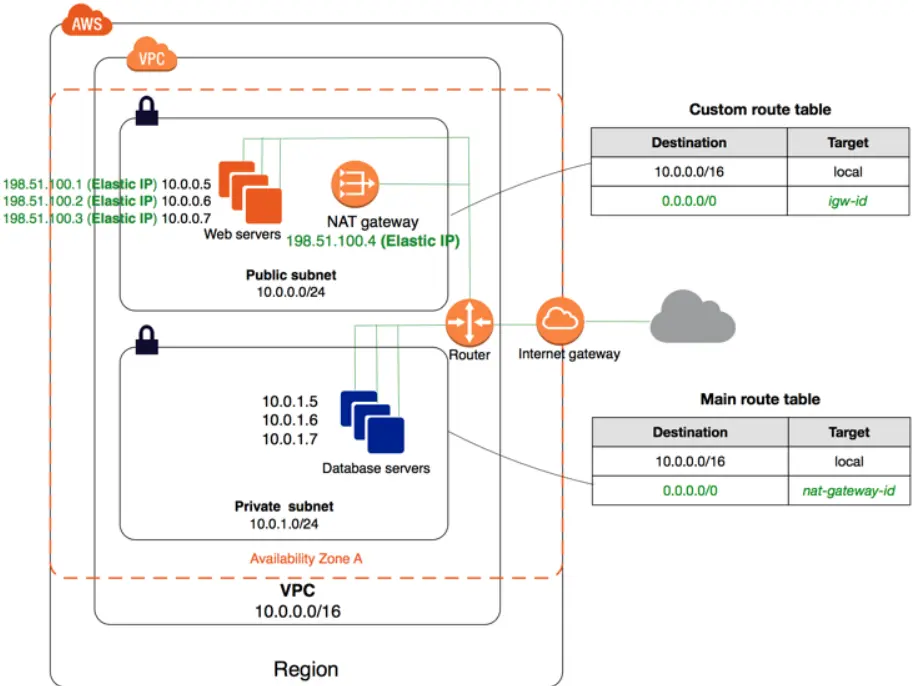
Credit: AWS
You can still specify whether to create a public or private connectivity type in AWS.
Before the NAT gateway, you needed to enable NAT for instances in a private subnet.
NAT Gateway vs NAT Instances: What’s The Difference?
A NAT instance is an EC2 instance that performs functions similar to those of a NAT gateway.
However, NAT instances differ from NAT gateways in that the latter is an AWS-managed service, while NAT instances are self-managed.
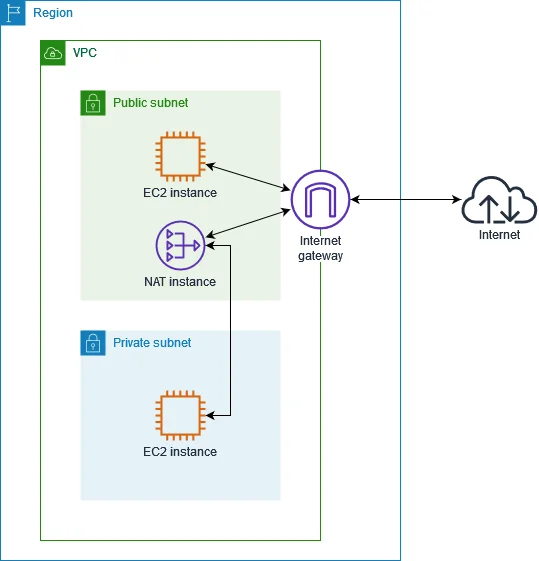
Credit: AWS
When you own a NAT instance, you do all the route configuration, rightsizing, and operating system and software updates. A NAT instance is like using an Amazon EC2 instance rather than Amazon RDS to host a database. It is ideal for advanced users who need this level of customization.
Other key differences include:
Feature | NAT gateway | NAT instance |
Performance | Automatically scales with traffic, no performance bottlenecks | Performance depends on EC2 instance type, manual scaling needed |
High availability | Built-in high availability across multiple AZs | High availability requires manual setup and management |
Cost | Usage-based pricing (data processed and hourly costs) | Cost depends on EC2 instance type; potentially cheaper for low traffic |
Security | Controlled through route tables and network ACLs | Directly apply security groups for granular control |
Setup and configuration | Simple setup, no ongoing management after initial configuration | Complex setup, ongoing management required |
Customization | Limited customization, suitable for standard use cases | Highly customizable, ideal for specific configurations |
Outbound traffic from private subnets to the internet through a NAT Gateway or NAT Instance is enabled by what we call an Internet Gateway.
What is the difference between NAT gateway and internet gateway?
An internet gateway (IGW) is a highly available, redundant, and horizontally scalable VPC component that enables communication between the internet and a VPC. Even if a Virtual Private Cloud had an IP address, none of its components would access the internet without an internet gateway.
Unlike a NAT gateway that has a per hour per gigabyte charge, an internet gateway does not attract charges. A NAT gateway connects the private subnet to the internet through the public subnet first and the internet gateway afterward. In contrast, an internet gateway directly connects the entire VPC to the internet.
This is how it looks visually:
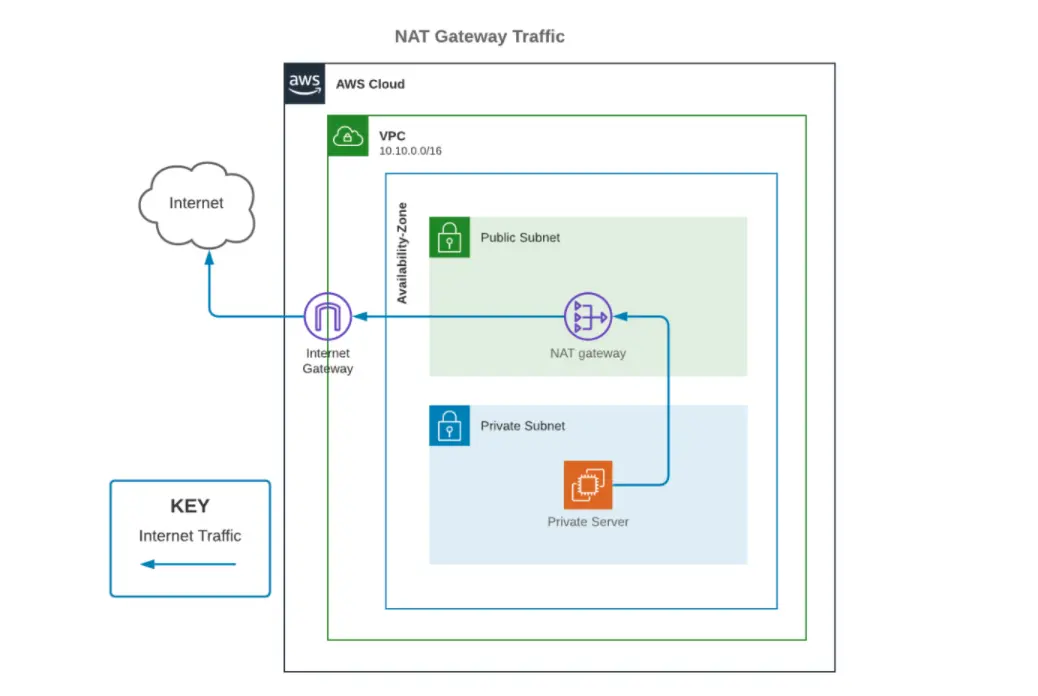
Credit: U-Turn Data
Still, while VPC owners create a NAT gateway within the public subnet, an internet gateway is like a router at the network’s edge.
Common AWS NAT Gateway Use Cases
Here are several scenarios where AWS NAT Gateway is a critical component.
Logging and monitoring
Applications frequently need to send logs or monitoring data to external services. With a NAT Gateway, private instances can communicate with these external systems securely, without being publicly exposed.
Database backups
Databases in private subnets often need to be backed up to external services or S3 buckets in different regions. NAT Gateway facilitates these backups securely, ensuring the database remains protected from public traffic.
Software updates and patching
Private instances often require downloading security patches or software updates. Using a NAT Gateway, these instances can access necessary update servers without opening inbound public traffic.
Package and dependency management
Developers working within private subnets might need to fetch libraries, dependencies, or Docker images from public repositories. NAT Gateway allows for this internet access without compromising the security of the private subnet.
Security compliance
Organizations with strict security policies may require instances to remain in private subnets while still needing internet access for specific tasks. NAT Gateway helps maintain these security boundaries, allowing necessary outbound traffic without exposing the instances.
Multi-region architectures
Applications distributed across different regions may need to communicate via public endpoints. NAT Gateway ensures secure outbound access for cross-region communication, shielding resources from the public Internet.
Outbound data transfer
Applications in private subnets may need to send data to external services, such as APIs or databases. NAT Gateway enables secure outbound communication, protecting the instances from direct public exposure.
Speaking of NAT charges, how much do NAT gateway data transfers cost in AWS?
How Does NAT Gateway Pricing Work?
AWS charges you per hour that a provisioned NAT gateway is available to you and per gigabyte of data transmitted through the provisioned NAT gateway. Think of that as a NAT gateway-hour and data processing charges for each gigabyte of data you transfer through the provisioned NAT gateway, regardless of the data’s origin or destination.
Also, AWS NAT gateway prices are region-specific and factor in availability zones, so the final price you receive will vary.
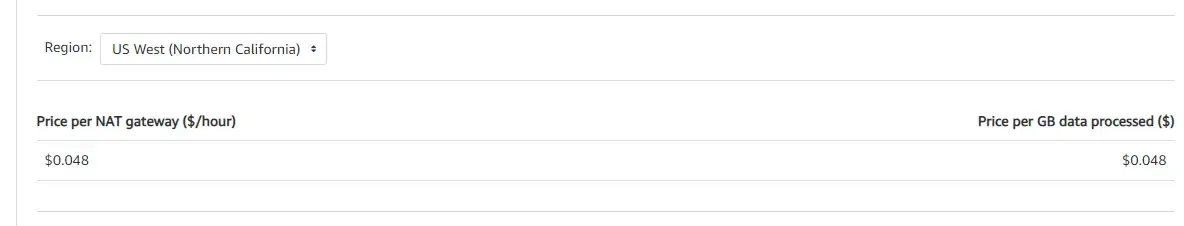
Also, AWS charges each partial hour used as a full hour consumed. There are also additional fees for standard data transfers through NAT gateways.
However, there are often cheaper alternatives depending on where you’re sending that data (inside of AWS or outside), your region, availability zone, and your security requirements.
Picture this. NAT gateway is like living in an apartment building with a doorman. People from the outside can mail you packages to your building’s address without knowing which apartment you live in. Your doorman will then route that package to your apartment.
However, every time you send or receive packages, you pay the doorman a fee. If you’re sending the package within your apartment community (Amazon), there are cheaper ways to do it.
Why Is NAT Gateway So Expensive?
Transmitting data with a NAT gateway can be expensive because there are multiple fees involved; hourly charge for using NAT gateway, data processing charge for NAT gateway, standard EC2 data transfer charge, and even more fees if you send data outside the Amazon ecosystem (the internet) through a NAT gateway.
Add all these factors together, and your NAT gateway costs can add up:
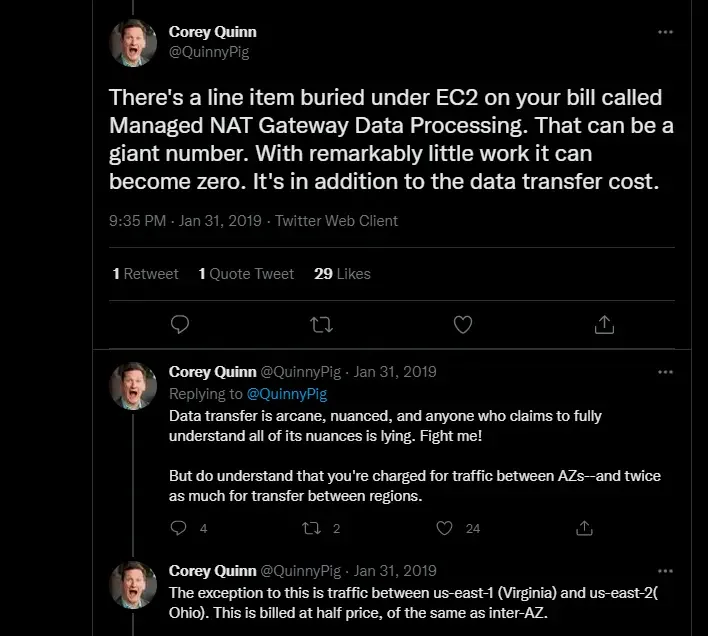
Credit: Corey Quinn on Twitter with tips to reduce AWS NAT gateway costs
In addition, some organizations forget that a NAT gateway is unnecessary to transfer data. Instead, you could set up and use a Type VPC endpoint gateway to avoid hourly and data processing fees when sending data to or from Amazon S3.
To reduce NAT gateway costs, you need to know what kind of data is being transferred and where it’s going. You can then start to replace some of them with cheaper options. We suggest starting with:
How To Reduce NAT Gateway Costs
1. Determine what types of data transfers occur the most

The best place to start is by figuring out which kinds of data transfers occur most in your organization. After this, you can better understand how to reduce NAT Gateway costs stemming from your company’s primary traffic source.
VPC Flow Logs hold details about your NAT gateway traffic, so you want to ensure that they are enabled. You can find instructions for that here. Next, navigate to the CloudWatch console and select Insights from the navigation panel. Click the dropdown to choose the log group linked to your NAT gateway.
Run the following script to determine which instances pass the most data through your NAT gateway. Note: x.x.x.x represents your NAT gateways private IP Address, while y.y. represents the first and second octets of the VPC CIDR range.
filter (dstAddr like ‘x.x.x.x’ and srcAddr like ‘y.y.’)
| stats sum(bytes) as bytesTransferred by srcAddr, dstAddr
| sort bytesTransferred desc
| limit 10
Run the following script to see what data your instances are sending to- or receiving from the internet.
filter (dstAddr like ‘x.x.x.x’ and srcAddr like ‘y.y.’)
or (srcAddr like ‘xxx.xx.xx.xx’ and dstAddr like ‘y.y.’)
| stats sum(bytes) as bytesTransferred by srcAddr, dstAddr
| sort bytesTransferred desc
| limit 10
Run the following script to see from which destinations your instances upload data to the most.
filter (srcAddr like ‘x.x.x.x’ and dstAddr not like ‘y.y.’)
| stats sum(bytes) as bytesTransferred by srcAddr, dstAddr
| sort bytesTransferred desc
| limit 10
Run the following script to see from which destinations your instances download data from the most.
filter (dstAddr like ‘x.x.x.x’ and srcAddr not like ‘y.y.’)
| stats sum(bytes) as bytesTransferred by srcAddr, dstAddr
| sort bytesTransferred desc
| limit 10
Once you’ve figured out where you’re transferring a lot of data, you’ll also want to figure out which AWS services they are using. In particular, you should know which ones are using Amazon S3 and AWS DynamoDB. This may require a little digging but will be helpful for the next steps.
2. Eliminate costly cross availability zone transfer charges

The next step to reduce NAT Gateway costs is to confirm that these high-traffic instances are within the NAT Gateway’s Availability Zone. If your instances are in a different availability zone from your NAT Gateway, you don’t have to delete your instances. Instead, create new NAT Gateways in the same availability zone as your instances.
Want to Reduce Your AWS Bill?
Our on-demand workshop has tons of tips and practical guidance!
3. Consider sending Amazon S3 and Dynamo traffic through gateway VPC endpoints instead of NAT Gateways

AWS offers free and low cost alternatives to NAT Gateway if you’re sending data within AWS. On example of that is VPC Endpoints. VPC Endpoints are a free alternative to NAT Gateway, but can only talk to S3 or DynamoDB.
If you’ve discovered that your NAT Gateway cost comprises data transfers to those two services within the same region, you can use these instructions to establish a Gateway VPC endpoint.
4. Consider setting up interface VPC endpoints instead of NAT Gateways for other Intra-AWS traffic

If you’re sending traffic to an AWS service that is not S3 or Dynamo DB, you can still use a lower cost alternative: Interface VPC endpoints. For a cost-savings estimate according to the number of VPC endpoints per availability zones, gigabytes of data processed, and your instances’ (or any other services’) regions, see here.
5. Depending on security requirements, consider replacing Your NAT Gateway with an internet gateway

For data transfers that are going to resources outside of AWS, you could potentially use an Internet Gateway. Like VPC endpoints, internet gateways are a no-cost alternative to NAT Gateways, but there are tradeoffs to consider.
One concern is that in order to use internet gateways, your instances must be in public subnets.
However, internet gateways have the added benefit of providing Internet Access Management (IAM) for added security through the use of security groups and network access control lists.
This approach can mitigate some risk. If you have a security team, you can talk to them about the best way to structure this.
Comparing AWS NAT Gateway With Alternatives: AWS Transit Gateway
AWS NAT Gateway and AWS Transit Gateway are both used to manage network traffic in AWS environments. However, they serve different purposes and are suited for different use cases.
Below is a quick comparison between these two services:
Feature | AWS NAT Gateway | AWS Transit Gateway |
Main purpose | Allows instances in private subnets to access the internet securely | Connects multiple VPCs, on-premises networks, and remote offices into a single, scalable hub |
Management | Fully managed by AWS, simple setup, no ongoing maintenance required | Fully managed by AWS, but requires more complex configuration and ongoing management |
Use case | Mainly used for outbound internet traffic from private subnets. | Used for connecting VPCs, enabling communication between different AWS accounts, and integrating with on-premises data centers |
Traffic type | Manages only outbound internet traffic from private subnets | Manages both inbound and outbound traffic, including VPC-to-VPC and VPC-to-on-premises |
Scalability | Automatically scales with outbound traffic requirements | Scales horizontally by adding more VPC attachments or peering connections |
High availability | Built-in high availability across multiple Availability Zones | High availability achieved through multiple Transit Gateway attachments and cross-region peering |
Security | Security controlled through route tables and network ACLs | Supports granular control over traffic routing and security, integrates with AWS security services like VPC peering and Direct Connect |
Cost | Usage-based pricing based on data processed and hourly costs | Pricing based on the number of VPC attachments, data processing, and hourly costs. Typically more expensive due to its broader capabilities. |
Integration with on-premises | Not designed for direct integration with on-premises networks | Integrates with on-premises networks via VPN or Direct Connect |
Custom routing | Limited to routing traffic to and from the internet for private subnets | Offers advanced routing capabilities, including inter-VPC traffic, on-premises traffic, and multi-region routing |
Can AWS NAT Gateway integrate with AWS Transit Gateway?
Yes. AWS NAT and Transit Gateway can integrate in complex AWS network architecture to offer comprehensive connectivity and routing solutions.
These include scenarios such as:
- In overlapping CIDR blocks, IP conflicts need to be managed across VPCs. NAT Gateway can be used for IP translation, and Transit Gateway for inter-VPC routing.
- In a multi-tenant SaaS environment, where each customer’s VPC is isolated. NAT Gateway manages overlapping IPs, while Transit Gateway connects these VPCs to shared services.
- In disaster recovery with cross-region failover, where a smooth failover is crucial, NAT Gateway maintains internet access. Transit Gateway, on the hand, handles traffic rerouting between regions.
- In hybrid cloud integration, where on-premises data centers need to connect with AWS. NAT Gateway resolves overlapping IPs, while Transit Gateway manages traffic between VPCs and on-premises networks.
- For centralized security inspection, where traffic needs to be routed through a security VPC, NAT Gateway handles IP management. Transit Gateway ensures that all traffic is centrally routed for inspection.
Catch, Control, And Optimize NAT Gateway Costs With CloudZero
The cost of data transfer through NAT gateways is one of the four horsemen of the big data apocalypse. Storage, shaping, and access to your data are the others.
Now picture this:
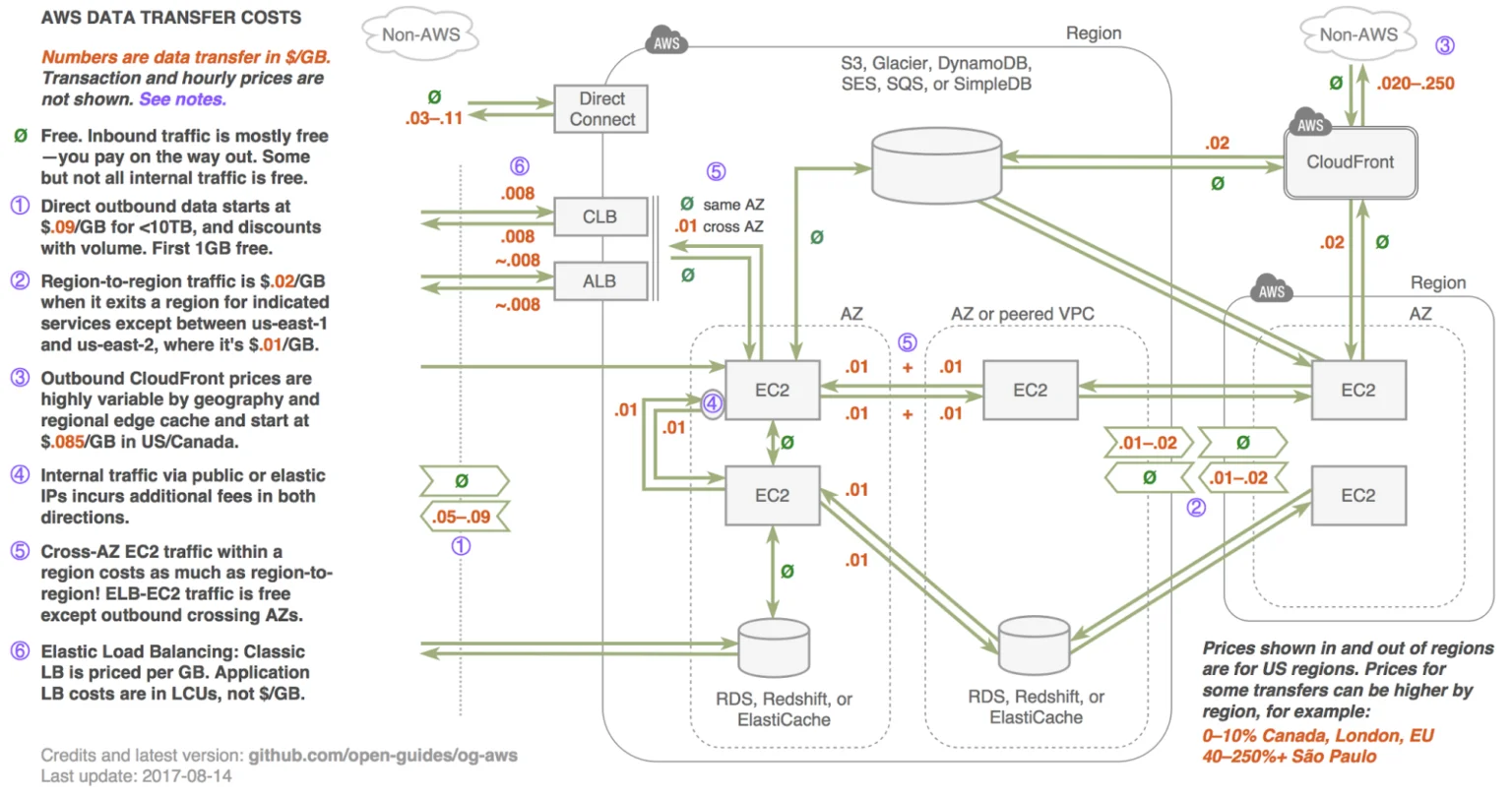
This image shows the many ways you could rack up data transfer costs in AWS. Some extremely complex rules govern data movement, making it difficult for companies to account for their costs.
The data’s highly variable and unpredictable nature does not make it any easier to link it to processes, products, or people that produce it. This makes it difficult to predict data transfer costs, for example.
With CloudZero, you can collect, analyze, and link data transfer costs, such as NAT gateway transfer costs, to the cost centers that generated them. This can not only help you forecast and allocate costs more accurately in AWS.
It can also empower you to determine which data transfer methods you can pause, change, or delete to lower costs without sacrificing data security during transmission.
With CloudZero’s cost anomaly detection, you are also notified immediately your AWS costs approach your set threshold, so you can avoid going over budget.
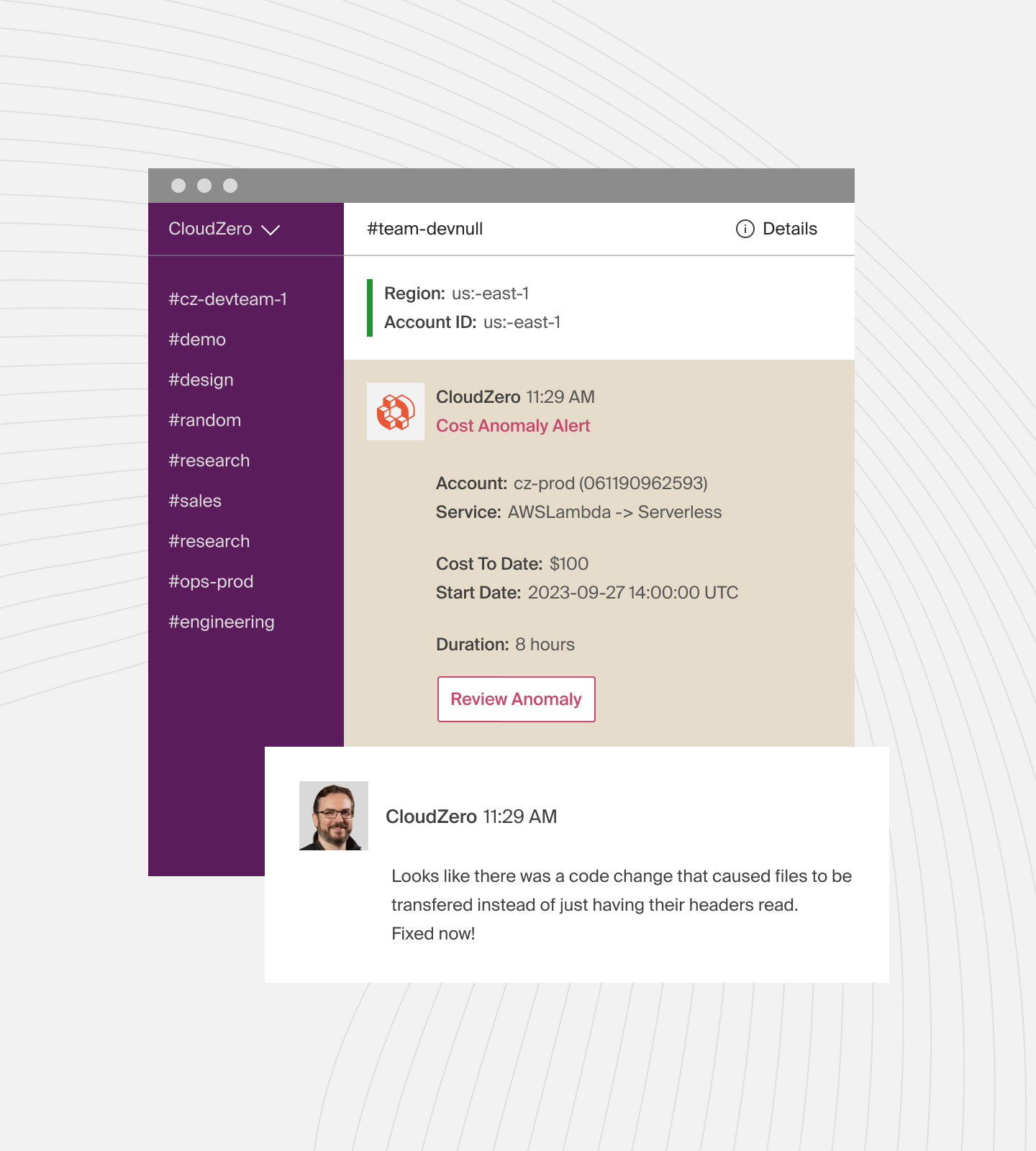
Want to see how CloudZero can save you money on data transfers?